Protect Your Cloud With Confidence
Protect Your Cloud With Confidence
Protect Your Cloud With Confidence
Protect Your Cloud With Confidence
Secure your cloud stack and manage compliance with confidence using Tatum CNAPP.
Secure your cloud stack and manage compliance with confidence using Tatum CNAPP.
Secure your cloud stack and manage compliance with confidence using Tatum CNAPP.
Secure your cloud stack and manage compliance with confidence using Tatum CNAPP.
Trusted by Leading Brands
Trusted by Leading Brands
Tatum CNAPP is trusted by sector leading enterprises across finance, technology and defense.
Tatum CNAPP is trusted by sector leading enterprises across finance, technology and defense.
Tatum CNAPP is trusted by sector leading enterprises across finance, technology and defense.
Our Valued Customers




















The Premiere Solution for Highly Regulated Industries and Hybrid Cloud Environments:
The Premiere Solution for Highly Regulated Industries and Hybrid Cloud Environments:
TATUM
CNAPP
TATUM
CNAPP







We're Leaders in Cloud Security
We're Leaders in Cloud Security
We're Leaders in Cloud Security
We're Korea’s Leaders in Cloud Security
Tatum CNAPP is built for enterprises operating complex cloud architecture in highly regulated industries.
Tatum CNAPP was built for enterprises operating complex cloud architecture in highly regulated industries.
Tatum CNAPP is built for enterprises operating complex cloud architecture in highly regulated industries.
Tatum CNAPP is built for enterprises operating complex cloud architecture in highly regulated industries.
Visualize Attack Paths and Threats Within the Cloud
Visualize Attack Paths and Threats Within the Cloud
Visualize Attack Paths and Threats Within the Cloud
Visualize Attack Paths and Threats Within the Cloud
Tatum CNAPP empowers you to visualize attack paths within your cloud infrastructure, allowing your security team to address threats from the attacker's perspective.
Tatum CNAPP empowers you to visualize attack paths within your cloud infrastructure, allowing security officers to address threats using the attacker's perspective.
Tatum CNAPP empowers you to visualize attack paths within your cloud infrastructure, allowing your security team to address threats from the attacker's perspective.



공격 경로와 위협을 한눈에


Custom Reporting
Custom Reporting
Custom Reporting
Security personnel can customize the results of cloud infrastructure diagnosis and treatment through the Tatum Security platform according to stakeholders.
The security officer can customize the results of cloud infrastructure diagnostics and actions through the Tatum Security Platform to suit stakeholders.
Security personnel can customize the results of cloud infrastructure diagnosis and treatment through the Tatum Security platform according to stakeholders.







With a simple field,
Discover & Settings
Discover & Config with simple query
With a simple field, Discover & Settings
In the Teytam Security Platform, you can easily search for all assets within the cloud infrastructure, create policies, define events, etc. through SQL-based query input.
In the Teytam Security Platform, you can easily search for all assets within the cloud infrastructure, create policies, define events, etc. through SQL-based query input.
In the Teytam Security Platform, you can easily search for all assets within the cloud infrastructure, create policies, define events, etc. through SQL-based query input.













Custom Reporting
Easily customize cloud diagnostics and automate reporting operations to meet your organization's needs.
Effortless Asset Discovery & Configuration
Locate assets, create policies, define events, and execute tasks with SQL-powered queries.



TATUM CNAPP
TATUM CNAPP
TATUM CNAPP
TATUM CNAPP
The Tatum CNAPP stands unmatched as the only cloud security solution fully equipped to meet Korea's unique security requirements.
The Tatum CNAPP stands unmatched as the only cloud security solution fully equipped to meet Korea's unique security requirements.
CSPM
CWPP
CIEM
KSPM
Real-Time
Threat Detection : CSPM
Achieve total visibility and maintain your compliance posture with TATUM CSPM.
Empower your security team to simplify operations with a unified platform—enabling the creation of robust cloud infrastructure policies and quick identification and remediation of misconfigurations.

Automated Reporting
Tatum CSPM's automated and customizable reporting feature streamlines reporting workflows and makes reporting effortless.
Manage Threat Prioritization
Identify your organization's critical vulnerabilities and make swift, priority-driven decisions with ease.
Revolutionizing Regulatory Compliance
Automate compliance with precision, adapting rules and policies to align with your regulatory and organization specific compliance needs.
Real-Time
Threat Detection : CSPM
Achieve total visibility and maintain your compliance posture with TATUM CSPM. Empower your security team to simplify operations within a unified platform—enabling the creation of robust cloud infrastructure policies and quick identification and remediation of misconfigurations.

Automated Reporting
Tatum CSPM's automated and customizable reporting feature streamlines reporting workflows and makes reporting effortless.
Manage Threat Prioritization
Identify your organization's critical vulnerabilities and make swift, priority-driven decisions with ease.
Revolutionizing Regulatory Compliance
Automate compliance with precision, adapting rules and policies to align with your regulatory and organization specific compliance needs.
Runtime Protection for your Cloud Workloads : CWPP
Strengthen workload security across hybrid and multi-cloud environments with ease. Gain full visibility, contextual insights, and superior defense capabilities.
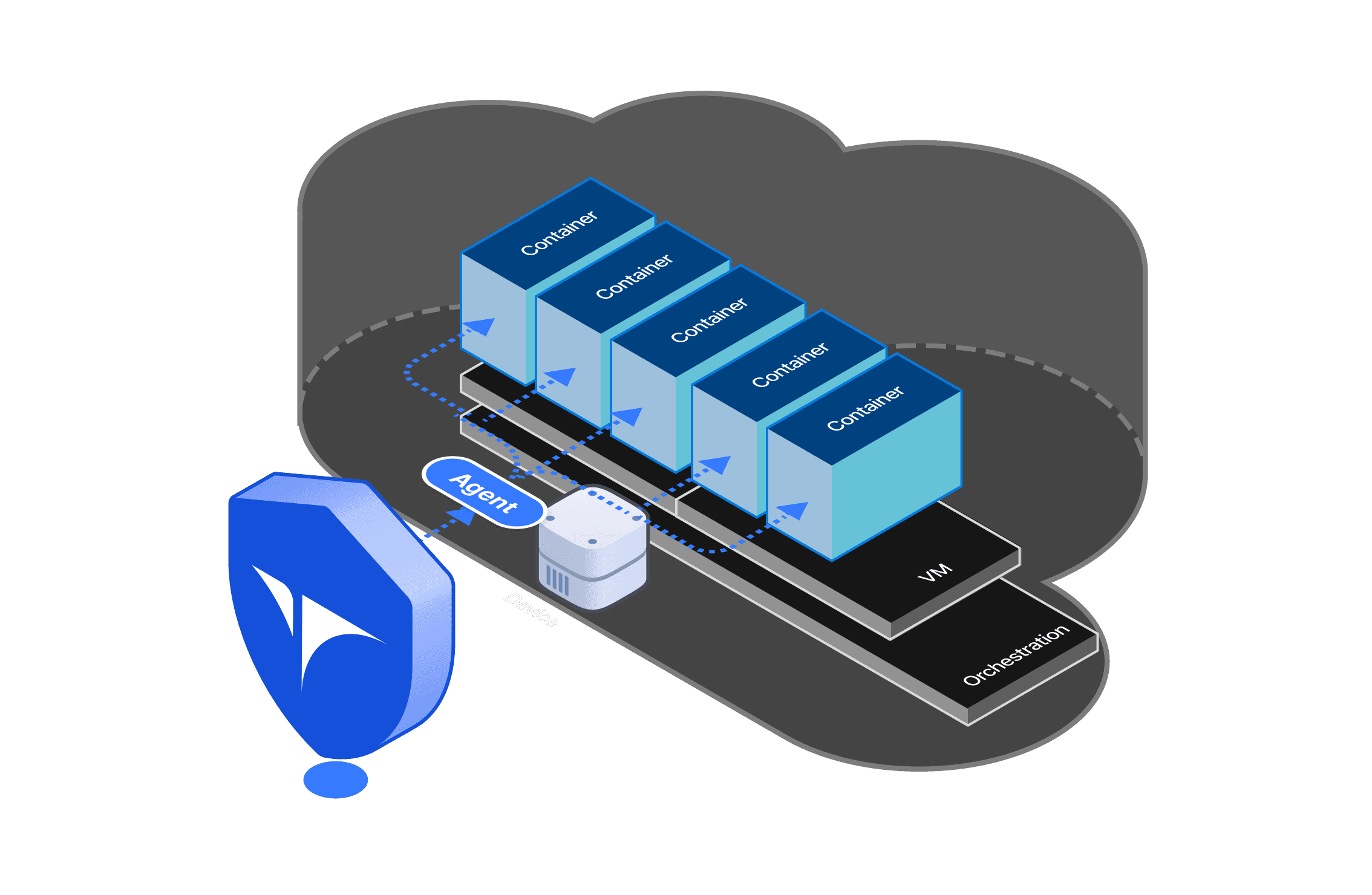
Custom Policy & Workload Protection
Achieve proactive threat management. Detect anomalies with user-defined rules aligned to the MITRE ATT&CK framework.
Image Scanning
Identify vulnerabilities (CVEs) in container images, including registry-stored images, and empower your security team with actionable insights.
Built on the Principle of Least Privilege : CIEM
Tatum CIEM enables efficient management of user identities, permissions, and roles in cloud environments. Security teams can identify and assign only the permissions necessary for tasks, minimizing unnecessary access, reducing attack surfaces, and ensuring secure, well-managed cloud infrastructure.
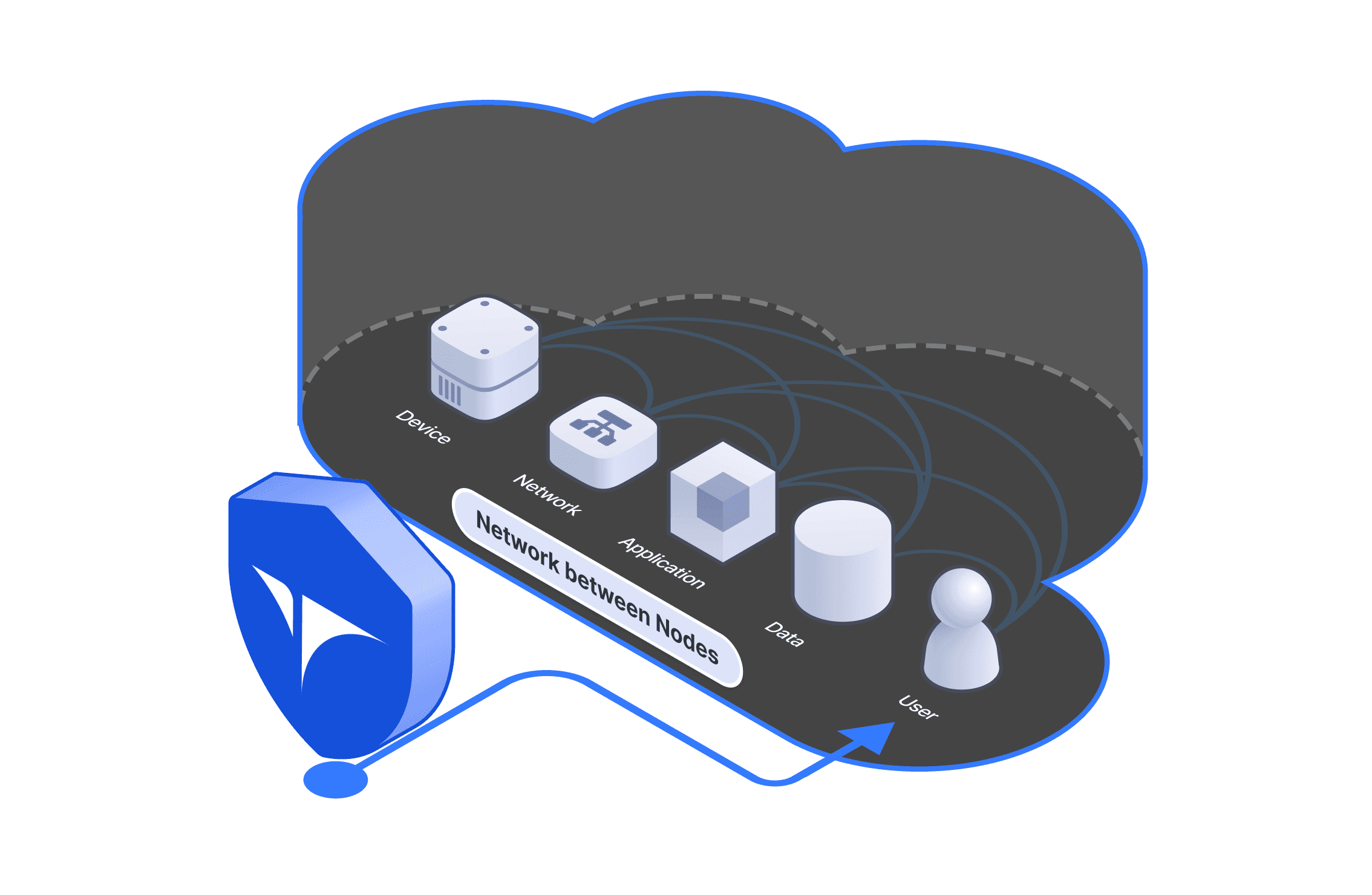
User Monitoring
Gain comprehensive visibility into user account activity, track behavior, and detect anomalies effectively.
Account Permission Management
Securely manage permissions for diverse user groups while maintaining robust account protection.
Optimized CSPM for Kubernetes Clusters: KSPM
Achieve comprehensive protection and ensure regulatory compliance across your K8s application portfolio with KSPM. Security professionals can now effectively manage and mitigate risks within K8s environments by leveraging Tatum’s advanced KSPM’s capabilities.

Real-Time
Threat Detection : CSPM
Achieve total visibility and maintain your compliance posture with TATUM CSPM. Empower your security team to simplify operations within a unified platform—enabling the creation of robust cloud infrastructure policies and quick identification and remediation of misconfigurations.

Automated Reporting
Tatum CSPM's automated and customizable reporting feature streamlines reporting workflows and makes reporting effortless.
Manage Threat Prioritization
Identify your organization's critical vulnerabilities and make swift, priority-driven decisions with ease.
Revolutionizing Regulatory Compliance
Automate compliance with precision, adapting rules and policies to align with your regulatory and organization specific compliance needs.
Runtime Protection for your Cloud Workloads : CWPP
Strengthen workload security across hybrid and multi-cloud environments with ease. Gain full visibility, contextual insights, and superior defense capabilities.

Custom Policy & Workload Protection
Achieve proactive threat management. Detect anomalies with user-defined rules aligned to the MITRE ATT&CK framework.
Image Scanning
Identify vulnerabilities (CVEs) in container images, including registry-stored images, and empower your security team with actionable insights.
Built on the Principle of Least Privilege : CIEM
Tatum CIEM enables efficient management of user identities, permissions, and roles in cloud environments. Security teams can identify and assign only the permissions necessary for tasks, minimizing unnecessary access, reducing attack surfaces, and ensuring secure, well-managed cloud infrastructure.

User Monitoring
Gain comprehensive visibility into user account activity, track behavior, and detect anomalies effectively.
Account Permission Management
Securely manage permissions for diverse user groups while maintaining robust account protection.
Optimized CSPM for Kubernetes Clusters: KSPM
Achieve comprehensive protection and ensure regulatory compliance across your K8s application portfolio with KSPM. Security professionals can now effectively manage and mitigate risks within K8s environments by leveraging Tatum’s advanced KSPM’s capabilities.

Real-Time
Threat Detection : CSPM
Achieve improved visibility and compliance through Tatum CSPM. Security personnel can orchestrate all tasks within our integrated platform, setting robust policies for cloud infrastructure and quickly identifying misconfigurations.


Automated Reporting
To achieve effective communication between stakeholders,
Term CSPM provides automated reporting functionality
and is stocked.
Increase efficiency with Tatum CSPM’s automated reporting that includes diagnostic data, links to documentation and remedial measures for addressing misconfigurations and threats.
Manage Threat Prioritization
Enable Security Officers to make decisions quickly based on what’s important by designating key threats faced by your organization as priorities.
Revolutionizing Regulatory Compliance
Automate compliance tasks to ensure precise adherence to diverse regulatory standards and frameworks, customizing rules and policies as needed to seamlessly align with your organization's specific requirements.
Runtime Protection for your Cloud Workloads : CWPP
Easily improve cloud workload protection across hybrid and multi-cloud environments and achieve a superior defense with comprehensive visibility and contextual insights.


User Define Rule & Protect Workloads
Custom Policy & Workload Protection
Achieve proactive threat management. Detect anomalies with user-defined rules aligned to the MITRE ATT&CK framework.
Image Scanning
Easily scan and manage Docker and Open Container images to ensure they comply with regulatory and security benchmarks.
Identify vulnerabilities (CVEs) in images inside the registry, including container images, and provide information for analysis and action by responsible parties.
Built on the Principle of Least Privilege : CIEM
Tatum CIEM enables efficient management of user identities, permissions, and roles in cloud environments. Security teams can identify and assign only the permissions necessary for tasks, minimizing unnecessary access, reducing attack surfaces, and ensuring secure, well-managed cloud infrastructure.
Smoothly manage user IDs, permissions and qualifications within your cloud environment. Using Tatum CIEM, security personnel can assign the permissions needed for work in accordance with the principle of least privilege, reduce unnecessary permissions to minimize your organization's attack surface, and effectively manage your cloud environment.


User monitoring
Gain comprehensive visibility into user account activity, track behavior, and detect anomalies effectively.
Account Permission Management
Securely manage permissions for diverse user groups while maintaining robust account protection.
Get Clear Visibility to K8s : KSPM
Achieve comprehensive protection and ensure regulatory compliance across your K8s application portfolio with KSPM. Security professionals can now effectively manage and mitigate risks within K8s environments by leveraging Tatum’s advanced KSPM’s capabilities.


Fast Integration
With Any Provider or Third-party Service
Fast Integration
With Any Provider or Third-party Service
Fast Integration
With Any Provider or Third-party Service
Fast Integration With Any Provider or Third-Party Service
Attain comprehensive security with unparalleled flexibility through easy integration with any private or public cloud provider,
and your chosen third-party services, at no additional cost.
Achieve comprehensive security with unparalleled flexibility through easy integration with any private or public cloud provider, and your chosen third-party services, at no additional cost.
Attain comprehensive security with unparalleled flexibility through easy integration with any private or public cloud provider,
and your chosen third-party services, at no additional cost.
Compatible with Private and Public Clouds
Compatible with Private and Public Clouds
Public Cloud


























Private Cloud
















Integrate with your frequently Third-Party solutions
Integrate with your frequently Third-Party solutions







Don’t chase.
Lead the way.
When it comes to security, don’t chase.
Lead the way.
When it comes to security, don’t chase.
Lead the way.
When it comes to security, don’t chase.
Lead the way.
Proactively addresses cloud security threats with Tatum Security's Cloud Native Application Protection Platform.
Proactively addresses cloud security threats with Tatum Security's Cloud Native Application Protection Platform.

Business Registration Number 277-81-01840 | CEO : Yang Hyuk-jae
11-10, 8th Floor, Teheran-ro 77-gil, Gangnam-gu, Seoul (Samseong-dong, Somang Building)
Mail Order Business Registration: No. 2021-Seoul Seocho-3149 Check Business Information
Phone Number: 02-6949-2446
©2024 Tatum Security. All rights reserved.

Business Registration Number 277-81-01840 | CEO : Yang Hyuk-jae
11-10, 8th Floor, Teheran-ro 77-gil, Gangnam-gu, Seoul (Samseong-dong, Somang Building)
Mail Order Business Registration: No. 2021-Seoul Seocho-3149 Check Business Information
Phone Number: 02-6949-2446
©2024 Tatum Security. All rights reserved.

Business Registration Number 277-81-01840 | CEO : Yang Hyuk-jae
11-10, 8th Floor, Teheran-ro 77-gil, Gangnam-gu, Seoul (Samseong-dong, Somang Building)
Mail Order Business Registration: No. 2021-Seoul Seocho-3149 Check Business Information
Phone Number: 02-6949-2446
©2024 Tatum Security. All rights reserved.

Business Registration Number 277-81-01840 | CEO : Yang Hyuk-jae
11-10, 8th Floor, Teheran-ro 77-gil, Gangnam-gu, Seoul (Samseong-dong, Somang Building)
Mail Order Business Registration: No. 2021-Seoul Seocho-3149 Check Business Information
Phone Number: 02-6949-2446
©2024 Tatum Security. All rights reserved.







